Microsoft Entra application
- # Introduction
- # Registering an application with Microsoft Entra ID
- # Adding permissions to the application
- # Granting tenant-wide admin consent to the application
- # Setting up authentication
- # Limiting application permissions to specific Exchange Online mailboxes
Introduction
Microsoft Entra ID is a cloud-based identity and access management service that can be used to access external resources. Example resources include Microsoft 365, the Azure portal, and thousands of other SaaS applications.
One of the services that Microsoft Entra ID provides is the OAuth authorization services - Used by Microsoft 365 and other Microsoft applications to authorize access to APIs/resources.
In order to access APIs/resources, we need to create a Microsoft Entra application.
Registering an application with Microsoft Entra ID
- Sign in to the Microsoft Entra admin center.
- Browse to Identity > Applications > App registrations then select New registration.
- Name the application, for example "sendmail-app".
-
Select Register.

-
On the app's overview page, copy and save the Application (client) ID value and the Directory (tenant) ID value.
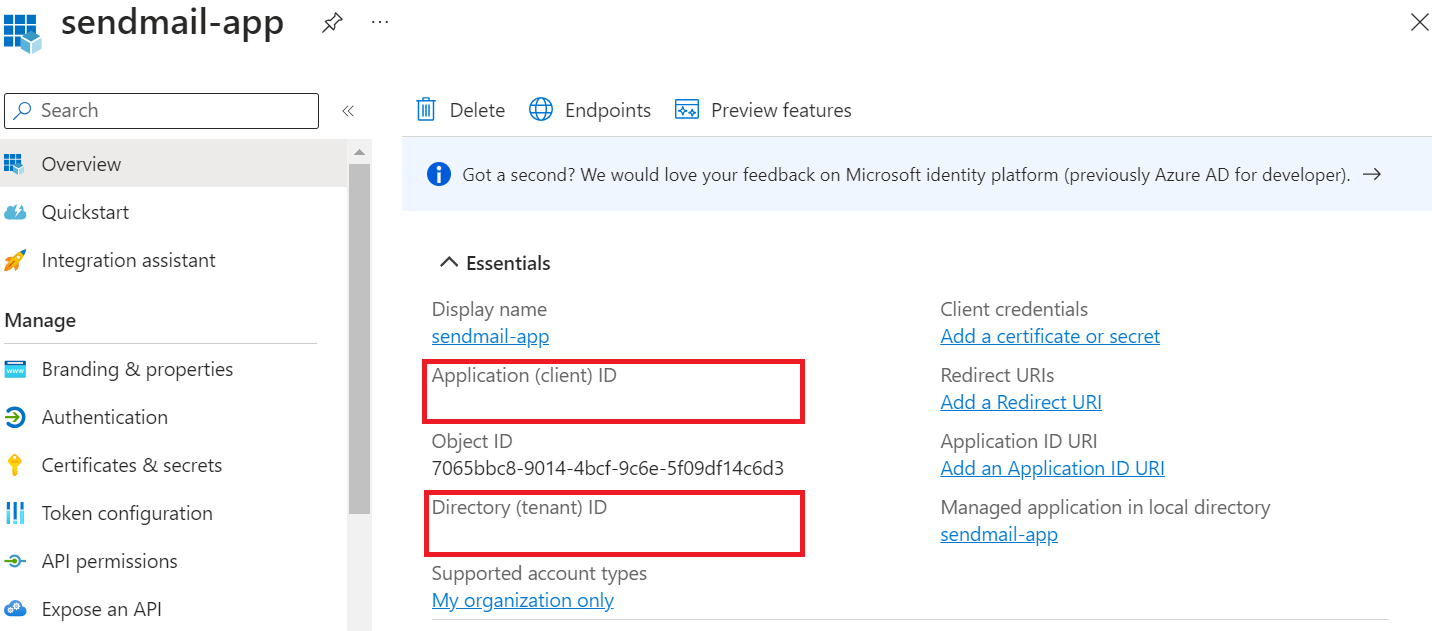
You've created your Microsoft Entra application.
Adding permissions to the application
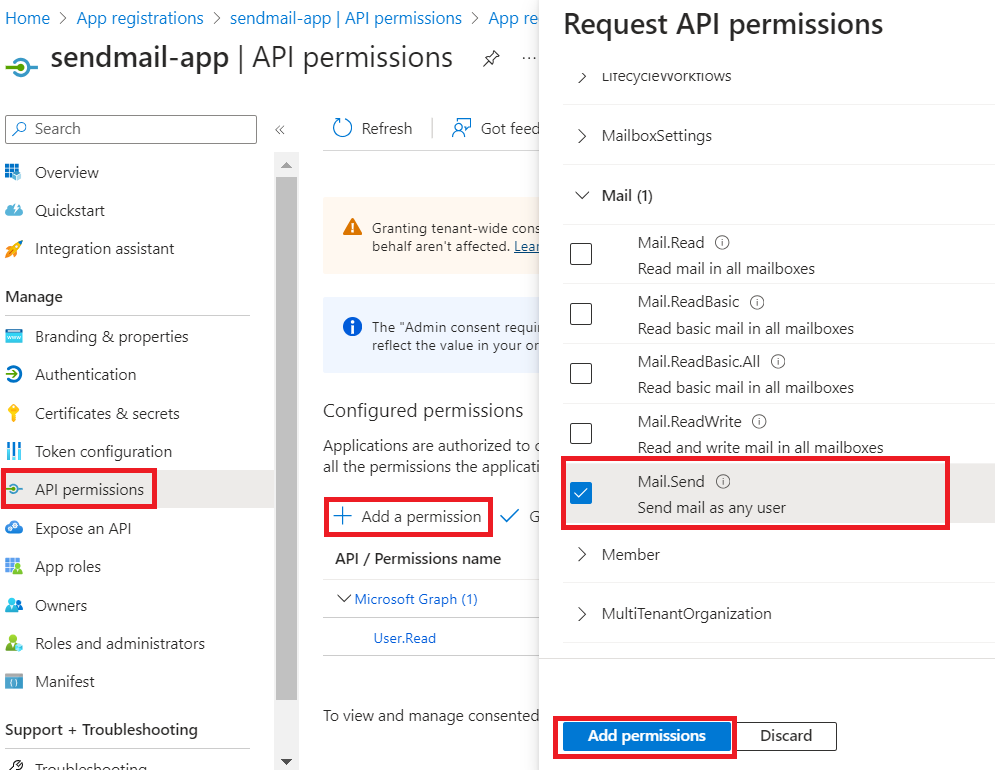
We must request access to the permissions in order for our app to function. We will need to request access for the Mail.Send permission. The permission allows the app to send mail as any user without a signed-in user.
- Locate the API permissions pane and select Add a permission.
- Select Microsoft Graph.
- Select Application permissions.
- In the Select Permissions dialog, choose the Mail.Send permission to configure to the app.
-
Select Add permissions.
Granting tenant-wide admin consent to the application
We are required to grant tenant-wide admin consent to an application in Microsoft Entra ID.
When we grant tenant-wide admin consent to the application, we give the application access to the permissions requested on behalf of the whole organization.
To grant admin consent, select Grant admin consent on the app's API permissions page.

Setting up authentication
To create password-based authentication (application secret):
- Select Certificates & secrets.
- Select Client secrets, and then Select New client secret.
- Provide a description of the secret, and a duration.
- Select Add.
Once you've saved the client secret, the value of the client secret is displayed. This is only displayed once, so copy and save this value.

Limiting application permissions to specific Exchange Online mailboxes
The Mail.Send application permission allows the app to send mail as any user without a signed-in user.
There are scenarios where administrators may want to limit an app to only specific mailboxes and not all Exchange Online mailboxes in the organization. Administrators can identify the set of mailboxes to permit access by putting them in a mail-enabled security group. Administrators can then limit third-party app access to only that set of mailboxes by creating an application access policy for access to that group.
To configure an application access policy by using the New-ApplicationAccessPolicy PowerShell cmdlet:
- Connect to Exchange Online PowerShell. For details, see Connect to Exchange Online PowerShell.
-
Identify the app's client ID and a mail-enabled security group to restrict the app's access to.
- Identify the app's application (client) ID that we previously saved from the the app's overview page.
- Create a new mail-enabled security group or use an existing one and identify the email address for the group.
-
Create an application access policy.
Run the following command, replacing the arguments for AppId, PolicyScopeGroupId, and Description.
1New-ApplicationAccessPolicy -AppId e7e4dbfc-046f-4074-9b3b-2ae8f144f59b -PolicyScopeGroupId SystemUsers@example.com -AccessRight RestrictAccess -Description "Restrict this app to members of distribution group SystemUsers." -
Test the newly created application access policy.
Run the following command, replacing the arguments for Identity and AppId.
1Test-ApplicationAccessPolicy -Identity support@example.com -AppId e7e4dbfc-046-4074-9b3b-2ae8f144f59bThe output of this command will indicate whether the app has access to support's mailbox.